Preventive GitHub Action | 25/11/2025 12:00PM EST.
We are releasing a GitHub Action provided to detect and actively prevent further infections in your organizations.
To use it, add a call to this action right before your build step (npm ci / npm install) - and you’re done!
Check it out here:https://github.com/RivalSecurity/sha1-hulud-prevention
–––
A new wave of activity consistent with the Shai Hulud supply chain attack pattern is emerging right now. Early evidence shows unauthorized repositories appearing inside GitHub organizations, exposure of secrets, and suspicious replication patterns that look nearly identical to the original incident.
The original Shai Hulud campaign harvested developer and CI tokens, then created new repositories inside victims' accounts containing exfiltrated secrets. What we are seeing today appears to follow the same playbook, which suggests that this is either a resurgence or a copycat event.
What We Know So Far
Recent analysis has provided critical clarity on several aspects of the Shai-Hulud malware, detailing mechanics that were previously not fully understood:
- Disguised Payload:
The payload is concealed within a large, obfuscated file namedbun_environment.js, which is designed to mimic a legitimate internal Bun runtime artifact.
- Secrets Exfiltration via Victim's GitHub:
The malware exfiltrates harvested secrets from the machine using trufflehog. Using the stolen GitHub credentials, It then creates a new public repository within the victim's own GitHub account. The malware then uploads all the victim's secrets into the repository, using a double-base64 encoded format.
- Self-Contained Persistence:
In some infections, the malware establishes persistence by registering a rogue self-hosted GitHub Actions runner named "SHA1HULUD" .
- Emergency File-Wiping:
A destructive failsafe is built into the malware. If both the secret exfiltration mechanism and the package publishing mechanism fail, the malware initiates file-wiping actions on the machine.
- Automated Cross-Account Propagation:
Once an npm or GitHub token is compromised, the malware automatically publishes malicious versions of every package the victim maintains. This is exactly why it spreads so rapidly.
- Preinstall Execution Hook:
The malicious loader (setup_bun.js) is triggered using npm's preinstall hook, triggering both in developer machines (npm installl) and CI workflows (npm ci).
https://github.com/search?q=Sha1-Hulud%3A+The+Second+Coming.&ref=opensearch&type=repositories
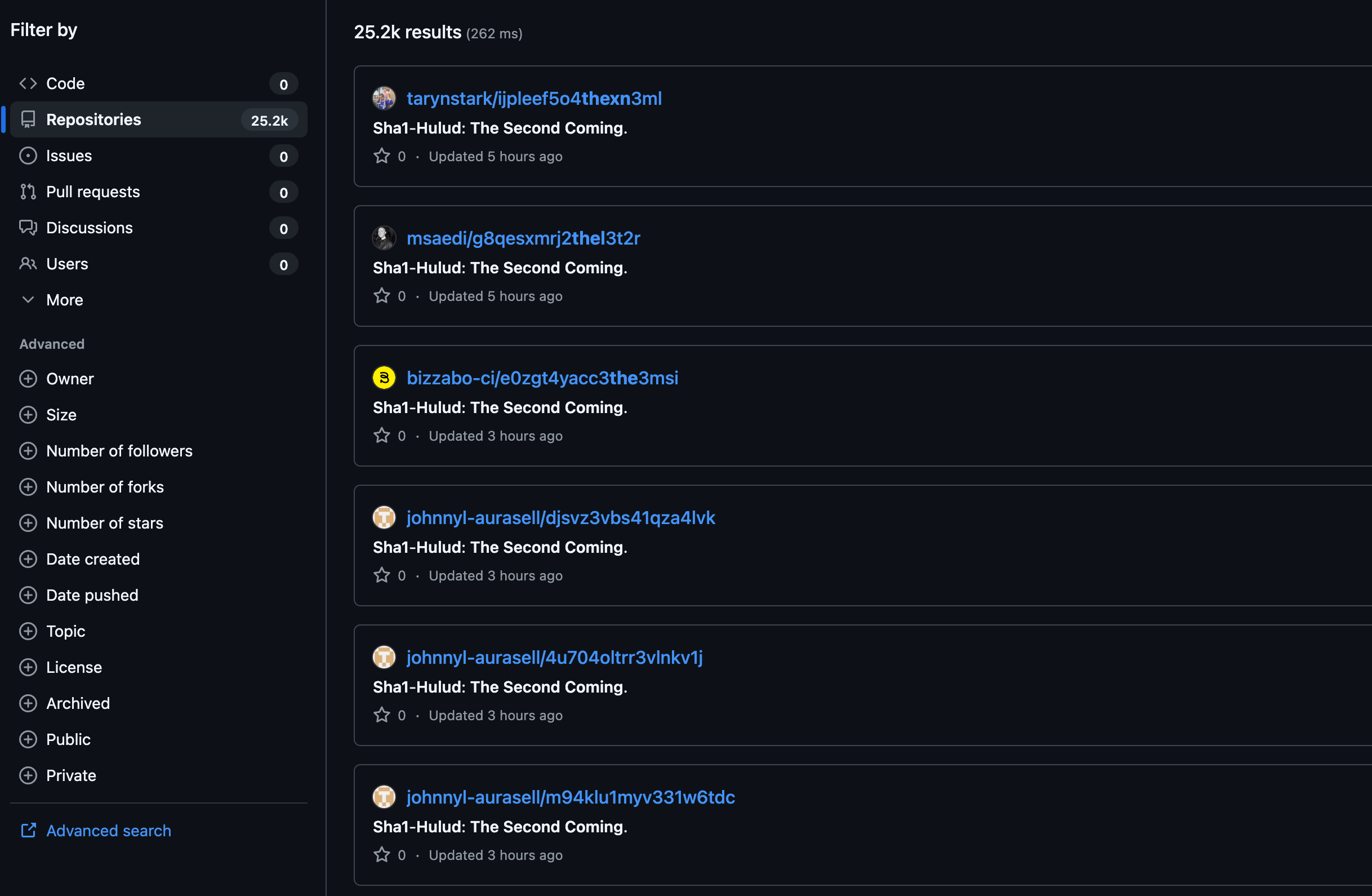

Immediate Actions to Take
- Search your GitHub organization for any repository you did not intentionally create, especially those that appear identical or were created recently - description usually contains the following text: "
Sha1-Hulud: The Second Coming." - Delete any suspicious repository immediately and rotate all secrets, tokens, and credentials found inside.
- Pause npm dependency updates and review all package changes from the last 24 hours.
- Treat any unexpected repository creation as a breach and activate internal incident response procedures.
This event is ongoing. Additional details and indicators of compromise are expected to surface.
This post will be updated as more information becomes available.
.jpeg)